OS11: Security
Including parts of Chapter 11 and Section 9.6.3 of [Hai19]
(Usage hints for this presentation)
This presentation is archived and will not receive further updates. Updated presentations on Operating Systems are available in the course IT Systems.
Computer Structures and Operating Systems 2023
Dr. Jens Lechtenbörger (License Information)
1. Introduction
1.1. OS Plan
- OS Overview (Wk 20)
- OS Introduction (Wk 21)
- Interrupts and I/O (Wk 21)
- Threads (Wk 23)
- Thread Scheduling (Wk 24)
- Mutual Exclusion (MX) (Wk 25)
- MX in Java (Wk 25)
- MX Challenges (Wk 25)
- Virtual Memory I (Wk 26)
- Virtual Memory II (Wk 26)
- Processes (Wk 27)
- Security (Wk 28)
Table of Contents
1.2. Today’s Core Questions
- How can I ensure that my downloaded software has not been manipulated?
- What is e-mail self-defense?
1.3. Learning Objectives
- Explain confidentiality and integrity as security goals
- Discuss differences between end-to-end and hop-by-hop goals
- Explain use of hash values and digital signatures for
integrity protection and discuss their differences
- Create and verify digital signatures (on e-mails and files/software)
1.4. Retrieval Practice
- Security — So far
- Hardware building blocks
- Kernel mode vs user mode:
Restrict instruction set
- Protect kernel data structures
- Enable access control via system call API
- Timer interrupts
- Transfer control periodically back to OS
- Kernel mode vs user mode:
Restrict instruction set
- Process as major OS abstraction
- Virtual address spaces
- Isolate processes from each other
- Access rights
- Virtual address spaces
- Hardware building blocks
1.4.1. Quiz on Hashing
1.5. Information Security
- Safety: Protection against unintended/natural/random events
- (Not focus here; requires proper management, involves training, redundancy, and insurances)
- Security: Protection against deliberate attacks/threats
- Protection of security goals for objects and services against attackers
1.5.1. Security Goals
- Classical security goals: CIA triad
- Confidentiality
- Only intended recipient can access information
- Typically guaranteed by encryption mechanisms
- (Or, e.g., with envelopes and protecting laws)
- Integrity
- Detection of unauthorized modification
- Typically guaranteed by cryptographic checksumming mechanisms
- (Or, e.g., with signatures and/or seals)
- Availability
- Information and functionality available when requested
- Supported by redundancy
- Further goals
- Accountability, authenticity, anonymity, (non-) deniability, …
- Confidentiality
1.5.2. Relativity
- Security is relative
- You need to define your goals and risks for specific pieces
of information, e.g.:
- How much confidentiality for course slides vs course exam?
- Apparently, it’s easy to keep the slides “secure”
- Harder for the exam
- Also: Who is the attacker with what resources?
- Select appropriate security mechanisms, typically with risk acceptance
- You need to define your goals and risks for specific pieces
of information, e.g.:
- Security via design process and management
- BSI (Germany) and ISO standards
- Topic in its own right
1.5.3. Attacker Models
- Sample classifications of attackers
- Strategy
- Targeted (specialized, looks for “weakest link”)
- E.g., espionage, blackmailing
- Opportunistic (standardized, looks for “weakest target”)
- E.g., phishing, extortion, bot/zombie creation (DDoS, spam, bitcoin mining, proxy)
- Targeted (specialized, looks for “weakest link”)
- Financial resources
- Compute capacity
- Time
- Knowledge (insider and position?)
- Strategy
1.6. Design Principles for Secure Systems
- Selected principles based on [SS75]
- Fail-safe defaults (whitelisting): If no explicit permission, then deny
- Least privilege (need to know): Subject has only those privileges that are necessary for given task
- Economy of mechanism: Security mechanisms should be as simple as possible
- Complete mediation: All accesses need to be checked
- Open design: Security should not depend on secrecy; instead open reviewing
- Separation of privilege: Permission not based on single condition
- Psychological acceptability: Security should not hinder usage
- And more, see [SS75] or [Hai19]
1.7. End-to-End Security
- Security goals may have varying scope
- Hop-by-hop
- End-to-end
- Integrity and confidentiality are end-to-end goals
- Beware: That’s not generally understood!
- (See next slide…)
- Consider hop-by-hop confidentiality
- Alice wants to send confidential message M to Bob via one hop, Eve
- Alice encrypts M for Eve, sends encrypted M to Eve
- Eve decrypts M, encrypts M for Bob, sends encrypted M to Bob
- Security gain or loss? (Compared to what?)
- Alice wants to send confidential message M to Bob via one hop, Eve
- Hop-by-hop integrity similarly
- Beware: That’s not generally understood!
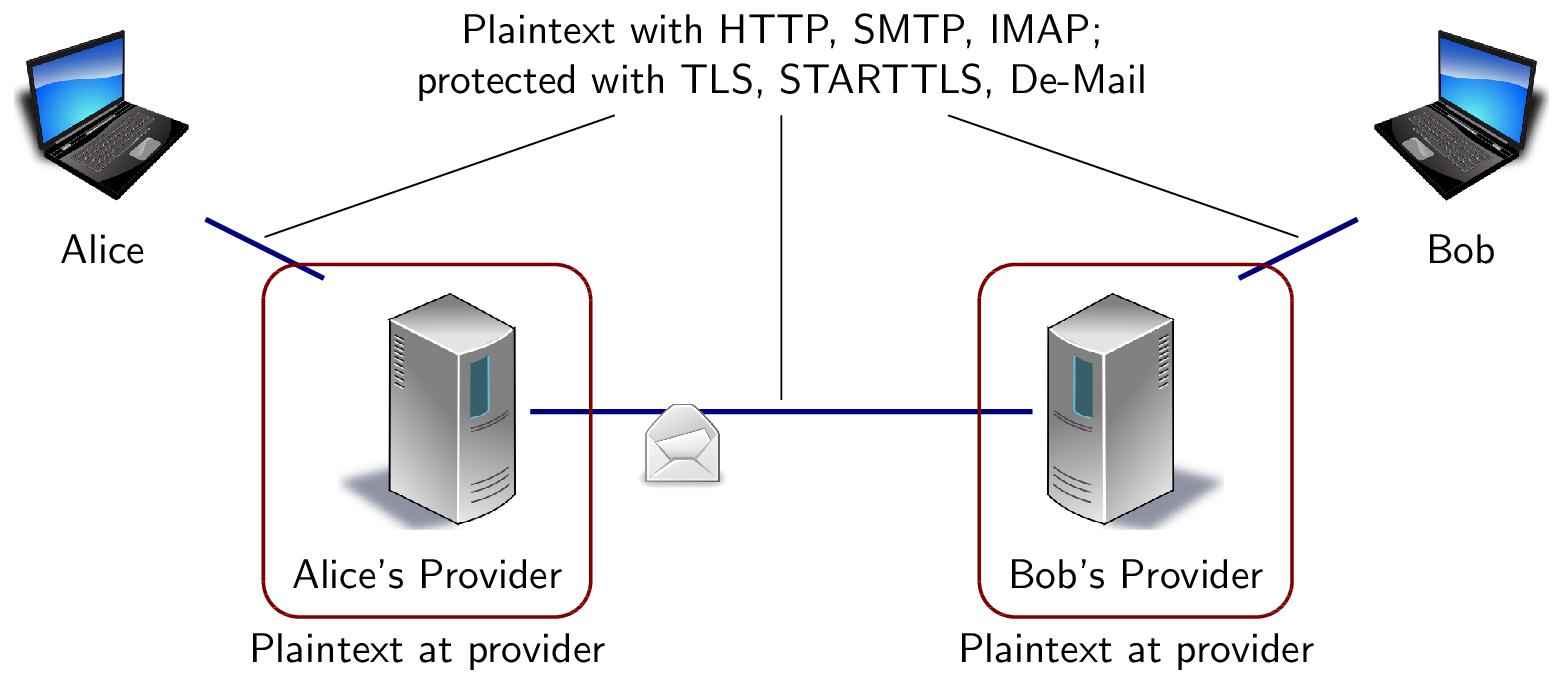
1.7.1. (Counter-) Example: De-Mail
De-Mail is a German approach defining legally binding, “secure” e-mail
![Hop-to-hop security of e-mail]()
- General picture
- Strong (hop-by-hop) security for each of the three blue links
- Plaintext at both providers (and
broken approach towards integrity, see [Lec11])
- End-to-end encryption allowed
- Digital signatures used in special cases
- General picture
2. Cryptography
2.1. Key Notions
- Cryptography = Art of “secret writing”
- Set of mathematical functions
- Cryptographic hash functions
- Classes of encryption algorithms
- Symmetric, secret key: en- and decryption use the same shared secret key
- Asymmetric, public key: participants own pairs of secret (decryption, signature creation) and public (encryption, signature verification) keys
- Hybrid: asymmetric initialization to establish symmetric keys for encryption
- Basis for various security mechanisms
- Performance
- Hashing > Symmetric Enc. > Asymmetric Enc.
- (One can hash more data per second than one can encrypt)
- (One can encrypt more data per second symmetrically than asymmetrically)
- Hashing > Symmetric Enc. > Asymmetric Enc.
2.1.1. Basic Assumptions
- Fundamental Tenet of Cryptography from [KPS02]
- “If lots of smart people have failed to solve a problem, then it probably won’t be solved (soon).”
- The problem to solve here: Break specific crypto algorithm
- If that did not happen for a long time, probably the algorithm is strong
- (Lots of crypto algorithms come without security proof)
- Kerckhoffs’ Principle (1883)
- Security of crypto systems should not depend upon secrecy of en- and decryption functions (but on secrecy of the used keys)
- “Open Design” principle from [SS75]
- Not respected in national security/military/intelligence
settings in Germany
- From Enigma through Libelle (approved for “Streng geheim”; developed by BSI, not published)
- Not respected in national security/military/intelligence
settings in Germany
- Opposite: Security through obscurity
2.1.2. Names
- Alice and Bob; Charlie, Carol, Dave, …
- Communicate frequently
- Value their privacy
- Have limited trust in third parties
- Appeared to be subversive individuals in the past
- Growing understanding in general public
- And, of course, politically correct names instead of “A” and “B”
- Eve, Mallory, Trudy
- Eavesdropper, malicious attacker, intruder
2.1.3. Notation
- M, C: Message and ciphertext (encrypted messages)
- K: Key (random bits, maybe with certain structure)
- E, D: En- and decryption functions
- KAB: Secret key shared between Alice and Bob
- KA-: Alice’s private key
- KA+: Alice’s public key
- K(M): Message M encrypted with key K (if function E is clear from context)
- [M]K: Message M signed with key K
2.2. GnuPG
- GNU Privacy Guard
- Free software for (e-mail) encryption and digital signatures
- Implementation of OpenPGP standard
- Secure e-mail based on hybrid cryptography
- In addition, lots of cryptographic algorithms via command line
gpg --version… gpg (GnuPG) 2.1.13 … Öff. Schlüssel: RSA, ELG, DSA, ECDH, ECDSA, EDDSA Verschlü.: IDEA, 3DES, CAST5, BLOWFISH, AES, AES192, AES256, TWOFISH, CAMELLIA128, CAMELLIA192, CAMELLIA256 Hash: SHA1, RIPEMD160, SHA256, SHA384, SHA512, SHA224
- Start by creating key pair:
gpg --gen-key
2.2.1. E-Mail Self-Defense
- My suggestion: Try out OpenPGP
- Create key pair, upload public key to server, send/receive encrypted (possibly signed) e-mails
- More specifically, follow Email Self-Defense
- GnuPG and Thunderbird
- Of course, other implementations exist
- The choice is yours
- Note: That guide contains instructions concerning the e-mail robot Edward, which can reply to your encrypted (and signed) test e-mails
2.3. (Cryptographic) Hash Functions
- Hash function
(or message digest)
- Input: Message M (bit string of arbitrary length)
- Output: Hash value H(M) (bit string of fixed length)
- Computation is one-way: Given H(M), we cannot compute M
- Collision: Different messages mapped to same hash value
- Cryptographic hash value ≈ digital fingerprint
- Collision resistant (different hash values for different messages)
- Weak collision resistance of hash function H
- Given message M it is computationally infeasible to generate
M’ such that H(M) = H(M’)
- (Computationally infeasible means that attackers should not be able to create collisions due to resource or time limitations)
- Given message M it is computationally infeasible to generate
M’ such that H(M) = H(M’)
- Strong collision resistance of hash function H
- Computationally infeasible to generate M and M’ such that H(M) = H(M’)
2.3.1. On Collision Resistance
- Later: Hash values are essence of
digital signatures
- Consider contract between Alice and Mallory
- “Mallory buys Alice’s used car for 20,000€”
- Contract’s text is message M
- Digital signatures of Alice and Mallory created from H(M)
- “Mallory buys Alice’s used car for 20,000€”
- Suppose H not weakly collision resistant
- Mallory may be able to create M’ with price of 1€ such that H(M) = H(M’)
- As H(M) = H(M’), there is no proof who signed what contract
- Consider contract between Alice and Mallory
- Birthdays, collisions, and probability
- Hash people to their birthdays (day and month, without year)
- (a) Weak collision resistance: Anyone sharing your birthday?
- (b) Strong collision resistance: Any pair sharing any birthday?
2.3.2. Sample Hash Applications
- Avoidance of plain text passwords
- Integrity tests
- Digital signatures
2.3.3. Sample Hash Standards
- MD4, MD5, SHA-1: Broken
SHA-1, SHA-2: Designed by NSA
- Bruce Schneier, 2004: “Algorithms from the NSA are considered a sort of alien technology: They come from a superior race with no explanations”
- Cryptographic hashing is extremely difficult, experts in 2006:
- 2017: SHA-1 broken (deprecated by NIST in 2011)
- Attack called SHAttered, see https://shattered.io/ if you are interested
- SHA-3 (aka Keccak),
standard since 2015
- Winner of public competition from 2007 to 2012
2.3.4. On Resource Limitations
- Previous slide mentions SHAttered
- In 2017, researchers demonstrated that SHA-1 is broken
- Sample results
- Brute force attack would have taken about 12,000,000 GPU years
- Researchers exploited weaknesses in SHA-1
- Their attack took 6,500 years of single-CPU computations and 110 years of single-GPU computations
- Computationally feasible on Google cloud infrastructure as of 2017
2.3.5. Sample Message and Fingerprints
Hi Bob, let's get started tomorrow! Best wishes Alice
- Sample hash values with GnuPG
gpg --print-md SHA1 alice.txt- alice.txt: 6FC1 F66C 598B D776 BA37 1A5C 2605 06CB 4CF9 0B89
gpg --print-md SHA256 alice.txt- alice.txt: 84E500CB 388EE799 05F50557 43C5481B 08B0BF17 1A2AE843 F4A197AD 2BA68D2E
- (Besides, specialized hashing tools exist, e.g.,
sha256sum)
2.4. Quiz
2.5. Symmetric Encryption
- Sender and recipient share secret key, KAB
- Encryption, by function E, of plaintext message M with KAB into ciphertext C
- C = E(KAB, M) (abbreviated to KAB (M) for agreed E)
- Bits of M and KAB are mixed and shuffled using reversible functions (e.g., XOR, bit shift)
- Simplest, yet provably secure case: One-time pad with XOR of random bit string and M
- C = E(KAB, M) (abbreviated to KAB (M) for agreed E)
- Decryption, by function D, with same key KAB
- M = D(KAB, E(KAB, M))
- Notice: Need to exchange secret key ahead of time
- Typical symmetric algorithms: AES, 3DES
2.6. Intuition of Asymmetric Encryption
- Participants own key pairs
- Private key, e.g., KB-: secret
- Public key, e.g., KB+: public / published
- En- and decryption based on “hard” mathematical problems
- Think of key pair as safe/vault with numeric key pad
- Open safe = public key
- Everybody can deposit messages and lock the safe
- Opening combination = private key
- Only the owner can open the safe and retrieve messages
- Open safe = public key
2.7. Asymmetric Encryption
- Participants own key pairs
- Private key, e.g., KB-: secret
- Public key, e.g., KB+: public / published
- Encryption of message for Bob with Bob’s public key
- C = E(KB+, M) = KB+ (M)
- Notice: No secret key exchange necessary
- Decryption with Bob’s secret key
- D(KB-, KB+(M)) = KB-(C) = M
- Notice: Only Bob can do this
- Challenge: Reliable distribution of public keys
- Solution: Certificates in Public Key Infrastructure, PKI
2.7.1. Sample Asymmetric Algorithms
- Diffie-Hellman Key Exchange (1976)
- RSA (Rivest, Shamir, Adleman 1978)
- Turing award 2002, most famous, PGP, GnuPG
- ElGamal (1985)
- Based on Diffie-Hellman, GnuPG and newer PGP variants
- Others more recently, e.g.:
- Elliptic curves with shorter keys, also GnuPG
- Post-quantum cryptography
- 4 standards
in 2022 based on NIST competition since 2016
- One of them, SIKE, found to be insecure in August 2022
- 4 standards
in 2022 based on NIST competition since 2016
2.7.2. Hybrid End-to-End Encryption
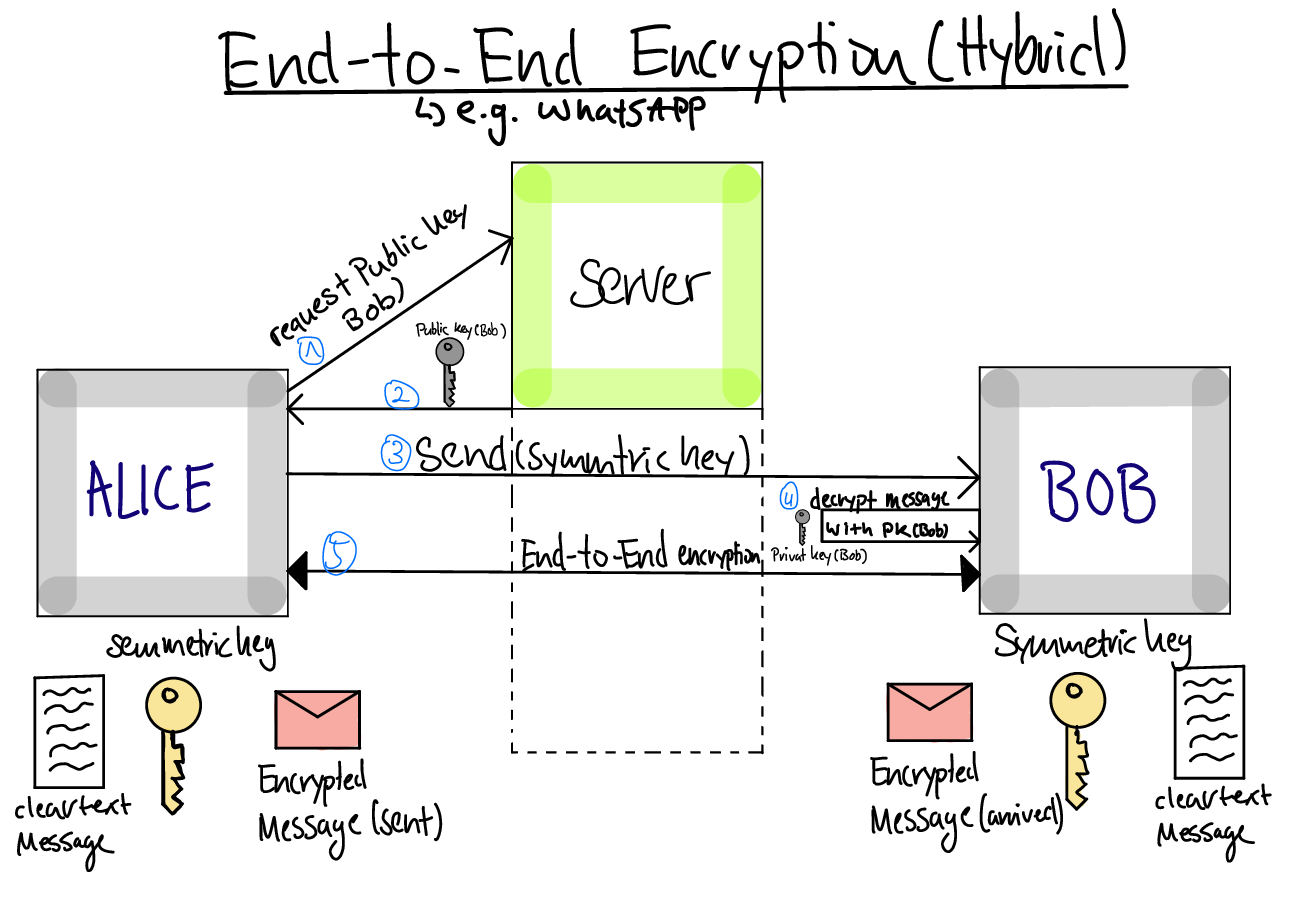
“End-to-End Encryption (Hybrid)” by Noah Lücke, Moritz van den Berg, Anton Levkau, Nick Vrban and Jannes Werk under CC BY-SA 4.0; converted from GitLab
2.7.3. GnuPG: Hybrid Encryption
- Create asymmetric key pair
gpg --gen-key- Various options/alternatives
- Encryption for Bob
gpg -e -a -r Bob file- Creates
file.asc; more precisely: - Creates random secret key KAB
- Symmetric encryption of file with KAB
- Specific algorithm obtained from Bob’s public key
- Asymmetric encryption of KAB with KB+
- Beware! No naïve encryption, but, e.g., PKCS #1
- Result: KB+(KAB) + KAB(file)
- (“+” between ciphertexts denotes string concatenation)
- Creates
3. Message Integrity
3.1. Situation and Goal
- Alice sends message M to Bob
- (Parts of) Network controlled by unknown parties (Eve and Mallory)
- Goals of integrity
- Bob is sure that M came from Alice
- Notice: Need authentication (proof of identity)!
- Bob can detect modifications to M
- Bob is sure that M came from Alice
- Non-goals: Alice cannot be sure
- that no third party receives M
- that Bob receives M
- that Bob receives M in unchanged form
3.2. General Idea
- Alice sends message along with its fingerprint
- Hint: A hash value is not good enough
- Instead: Use some ingredient that is unknown to the attacker
- Bob receives message and fingerprint and verifies whether
both match
- If message changed by Mallory, he cannot produce a matching fingerprint
- Typical techniques
- Message authentication codes
- E.g., Alice and Bob share secret KAB, concatenate that to message before hashing
- Digital signatures (next slides)
- Message authentication codes
3.3. Digital Signatures
- Based on asymmetric cryptography
- En- and decryption reversed
- Basic idea
- Signature created by encryption with private key: KA-(M)
- Only Alice can create this!
- Verification via decryption with public key: D(KA+, KA-(M))
- Everyone can do this as public key is public!
- Signature created by encryption with private key: KA-(M)
- Practice: Encrypt hash value of M, e.g., KA-(SHA-3(M))
- Recall
- Performance
- Hash collisions
- Recall
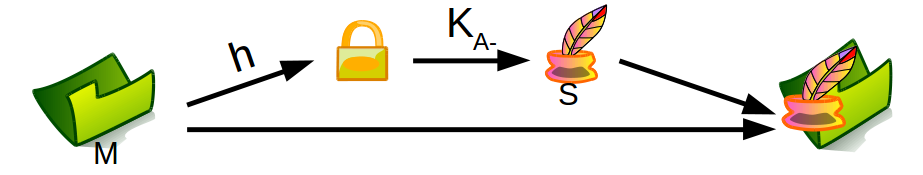
3.3.1. Some Details of Digital Signatures (1/2)
- Signing of M by Alice with private key KA-
- Signature S = KA-(h(M))
- Only Alice can do this
- Transmit signed message [M]KA- = M + S = message +
signature
- (“+” is concatenation)
- Signature S = KA-(h(M))
3.3.2. Some Details of Digital Signatures (2/2)
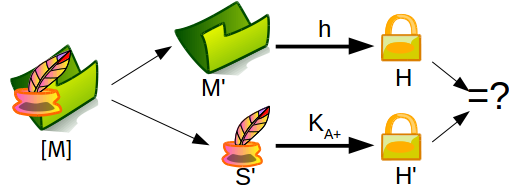
- [M] received by Bob
Verification whether [M] sent by Alice and unchanged along the way
![Verification of digital signature]()
- Split [M]: [M] = M’ + S’
- Hash M’: H = h(M’)
- Decrypt S’: H’ = KA+(S’)
- Bob needs public key of Alice to do this
- Everyone can do this
- Verify H = H’
3.3.3. GnuPG: Digital Signatures
gpg --sign -a -b alice.txt- Creates digital signature
alice.txt.ascfor inputalice.txt
- Creates digital signature
gpg --verify alice.txt.asc- Expects to be verified content as
alice.txt - Verifies signature
- Frequently used to verify integrity of downloads
- Expects to be verified content as
3.4. Electronic Signatures
- “Signatures” of varying legal impact in IT environments
- Different types, e.g., simple (e.g., sender’s name in e-mail), advanced (digital signature as discussed above), qualified
- Qualified electronic signatures may replace paper based signatures
(e.g., dismissal, invoice)
- Subset of advanced electronic signatures
- Based on qualified certificates (with qualified electronic signature, issued by accredited organization; law prescribes rules concerning infrastructure and processes)
- Created on secure signature-creation devices (nPA may store qualified certificate; additional reader necessary)
4. OS Context
4.1. Basic OS Security Services
4.1.1. Service Overview (1/2)
- Rights management, authorization
- Discussed already: Access rights
- What is Bob allowed to do?
- Discussed already: Access rights
- Logging
- Who did what when?
- (Not considered here)
- Basic cryptographic services
- Offering selection of above techniques: a/symmetric techniques, hashing
4.1.2. Service Overview (2/2)
- Identification/Authentication
- Identification: Claim of identity
- I’m Bob …
- Authentication: Proof of identity (more on subsequent slides)
- My password is “p@ssw0rd”
- (Bad idea, easily broken!)
- My password is “p@ssw0rd”
- Identification: Claim of identity
- Integrity protection
- E.g., installation and updates of software under GNU/Linux with apt
4.1.3. Authentication
- Proof of identity
- Something the individual knows
- Password, PIN, answer to security question
- Something the individual possesses
- Private key (on smartcard or elsewhere), iTAN
- Something the individual is
- Static biometrics, e.g., fingerprint, iris scan
- Something the individual does
- Dynamic biometrics, e.g., voice or typing pattern
- Something the individual knows
- Necessary prerequisite to enforce access rights
- Who is allowed to perform what operation on what resource?
4.1.4. Two-Factor Authentication
- Combinations of above categories
- Physical banking
- Bank card (possession) plus PIN (knowledge)
- Online banking
- Password for login (knowledge) plus mTAN or iTAN (possession)
- Beware: Must keep factors separate
- Do not record PIN on card
- Do not perform online banking on device that receives mTAN
- Physical banking
4.2. Key Security Best Practices
- Consult others
- Adopt a holistic risk-management perspective
- Deploy firewalls and make sure they are correctly configured
- Deploy anti-virus software
- Keep all your software up to date
- Deploy an IDS
- Assume all network communications are vulnerable
- … (see Sec. 11.8 in [Hai19])
5. Conclusions
5.1. Summary
- Security is complex, requires design and management
- Cryptography provides foundation for lots of security mechanisms
- Don’t implement cryptographic protocols yourselves!
- Use proven tools, e.g., GnuPG
- Asymmetric crypto with key pairs
- Public key for encryption and signature verification
- Private key for decryption and signature creation
- Hash functions and digital signatures for integrity
Bibliography
- [Hai19] Hailperin, Operating Systems and Middleware – Supporting Controlled Interaction, revised edition 1.3.1, 2019. https://gustavus.edu/mcs/max/os-book/
- [KPS02] Kaufman, Perlman & Speciner, Network Security: Private Communication in a Public World, Second Edition, Prentice Hall Press, 2002.
- [Lec11] Lechtenbörger, Zur Sicherheit von De-Mail, Datenschutz und Datensicherheit 35(4), 268-269 (2011).
- [SS75] Saltzer & Schroeder, The protection of information in computer systems, Proceedings of the IEEE 63(9), 1278-1308 (1975). http://web.mit.edu/Saltzer/www/publications/protection/
License Information
This document is part of an Open Educational Resource (OER) course on Operating Systems. Source code and source files are available on GitLab under free licenses.
Except where otherwise noted, the work “OS11: Security”, © 2017-2024 Jens Lechtenbörger, is published under the Creative Commons license CC BY-SA 4.0.
In particular, trademark rights are not licensed under this license. Thus, rights concerning third party logos (e.g., on the title slide) and other (trade-) marks (e.g., “Creative Commons” itself) remain with their respective holders.