OS Overview
(Usage hints for this presentation)
This presentation is archived and will not receive further updates. Updated presentations on Operating Systems are available in the course IT Systems.
Computer Structures and Operating Systems 2023
Dr. Jens Lechtenbörger (License Information)
1. Introduction
1.1. Recall: Big Picture of CSOS
- Computer Structures and Operating Systems (CSOS)
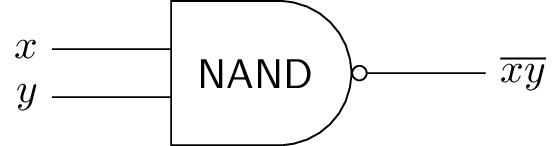
CS: How to build a computer from logic gates?
- Von Neumann architecture
CPU (ALU), RAM, I/O
- OS: What abstractions do Operating Systems provide for
applications?
Processes and threads with scheduling and concurrency, virtual memory
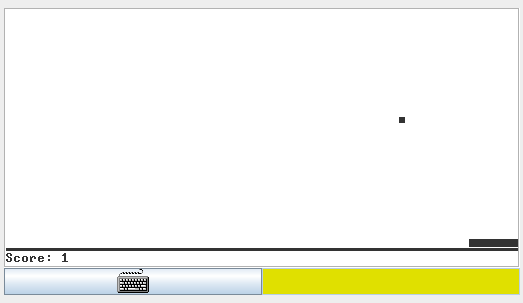
![Pong in TECS VM]()
“Pong in TECS VM” under GPLv2; screenshot of VM of TECS software suite
- What is currently executing why and where, using what resources how?
1.1.1. OS Responsibilities
What does your OS even do?
Figure © 2016 Julia Evans, all rights reserved; from julia's drawings. Displayed here with personal permission.
1.1.2. Definition of Operating System
- Definition from [Hai19]: Software
- that uses hardware resources of a computer system
- to provide support for the execution of other software.
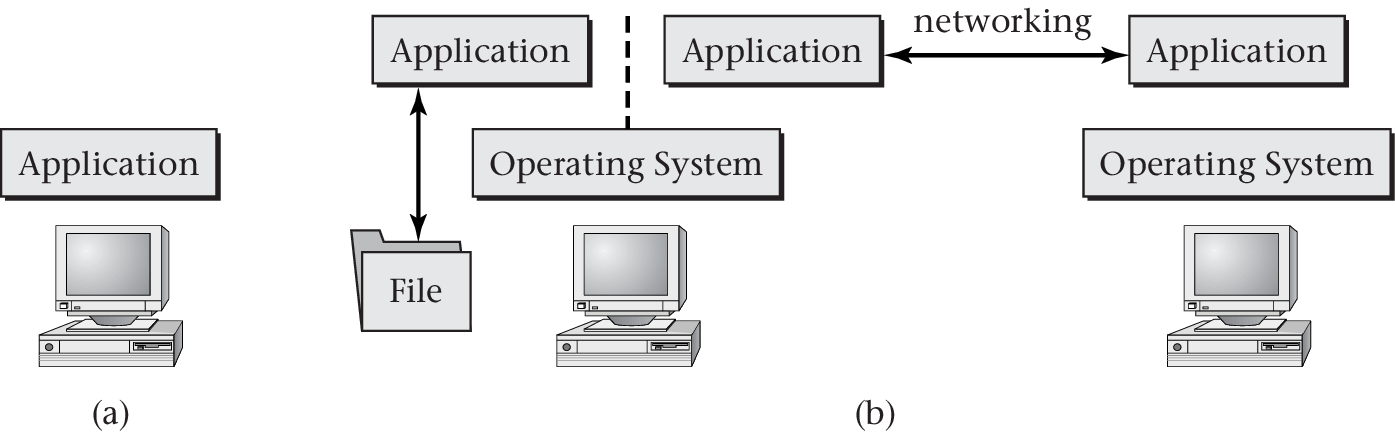
“Figure 1.1 of [Hai17]” by Max Hailperin under CC BY-SA 3.0; converted from GitHub
1.2. Prerequisite Knowledge
- Be able to write, compile, and execute small Java programs
- What is an object? What is the meaning of
thisin Java? - How do you execute a program that requires a command line argument?
- What is an object? What is the meaning of
- Be able to explain basic data structures (stacks, queues, trees) and algorithms (in particular, hashing)
- Being able to explain the database transaction concept and update anomalies
2. OS Teaching
2.1. OS Part
- Sharp cut ahead
- So far, we followed a book with projects to build a computer bottom up
- Unfortunately, nothing similar exists to build an Operating System
(OS) bottom up
- (Or is far too technical for our purposes)
- Thus, the OS part presents major concepts and techniques of modern OSs
- Some topics build upon each other
- Some are more isolated
- Goal: Understand and control your devices
- Performance
- Trust
2.2. OS Exercises
- While the CS part had weekly projects, this will not be the case for the OS part
- Exercise sheets continue, though
2.3. Textbook(s)
- Major source (adopted in 2017)
- [Hai19] Max Hailperin: Operating Systems and Middleware: Supporting Controlled Interaction
- Distributed under the free/libre and open license
CC BY-SA 3.0
- Source code at GitHub
- PDF (also) in Learnweb
- Distributed under the free/libre and open license
CC BY-SA 3.0
- [Hai19] Max Hailperin: Operating Systems and Middleware: Supporting Controlled Interaction
- Additions
2.4. Presentations (1/2)
- HTML presentations with audio for self-study
- Read usage hints first
- HTML generated from simple text files in Org mode
- Source code available on GitLab
- You may want to check out those for your annotations
- Generated presentations;
HTML and two PDF variants
- Those are draft versions until you see a link in Learnweb
- Offline use possible
- Generate yourself or download from latest GitLab pipeline
- Open Educational Resources (OER), your contributions are very welcome!
- Source code available on GitLab
2.5. Presentations (2/2)
- As usual, (pointers to) presentations are available in Learnweb
Presentations include
- Learning objectives
- Explanations for class topics
- Some slides contain audio explanations, e.g., the one starting with this bullet point
3. OS Plan
3.1. Big Picture of OS Sessions
3.2. A Quiz
Bibliography
- [Hai19] Hailperin, Operating Systems and Middleware – Supporting Controlled Interaction, revised edition 1.3.1, 2019. https://gustavus.edu/mcs/max/os-book/
- [Sta14] Stallings, Operating Systems – Internals and Design Principles, Pearson, 2014.
- [TB15] Tanenbaum & Bos, Modern Operating Systems, Pearson, 2015.
License Information
This document is part of an Open Educational Resource (OER) course on Operating Systems. Source code and source files are available on GitLab under free licenses.
Except where otherwise noted, the work “OS Overview”, © 2017-2023 Jens Lechtenbörger, is published under the Creative Commons license CC BY-SA 4.0.
In particular, trademark rights are not licensed under this license. Thus, rights concerning third party logos (e.g., on the title slide) and other (trade-) marks (e.g., “Creative Commons” itself) remain with their respective holders.