Processes
(Usage hints for this presentation)
IT Systems, Summer Term 2026
Dr.-Ing. Matthes Elstermann
1. Introduction
1.1. Core Questions
- What is a process?
- How are files represented by the OS, and how are they used for inter-process communication?
(Based on Chapter 7 and Section 8.3 of (Hailperin 2019))
1.2. Learning Objectives
- Explain process and thread concept
- Perform simple tasks in Bash (continued)
- View directories and files, build pipelines, redirect in- or
output, list processes with
ps
- View directories and files, build pipelines, redirect in- or
output, list processes with
- Explain file descriptors for commands and pipelines
- Explain access control, access matrix, and ACLs
- Use
chmodto modify file permissions
- Use
1.3. Retrieval practice
1.3.1. Previously on OS …
- What are processes and threads?
- What is a thread control block?
- What are system calls?
- How to execute shell commands as part of The Command Line Murders?
1.3.2. Quiz 1
1.3.3. Quiz 2
1.3.4. Quiz 3
Agenda
2. Processes
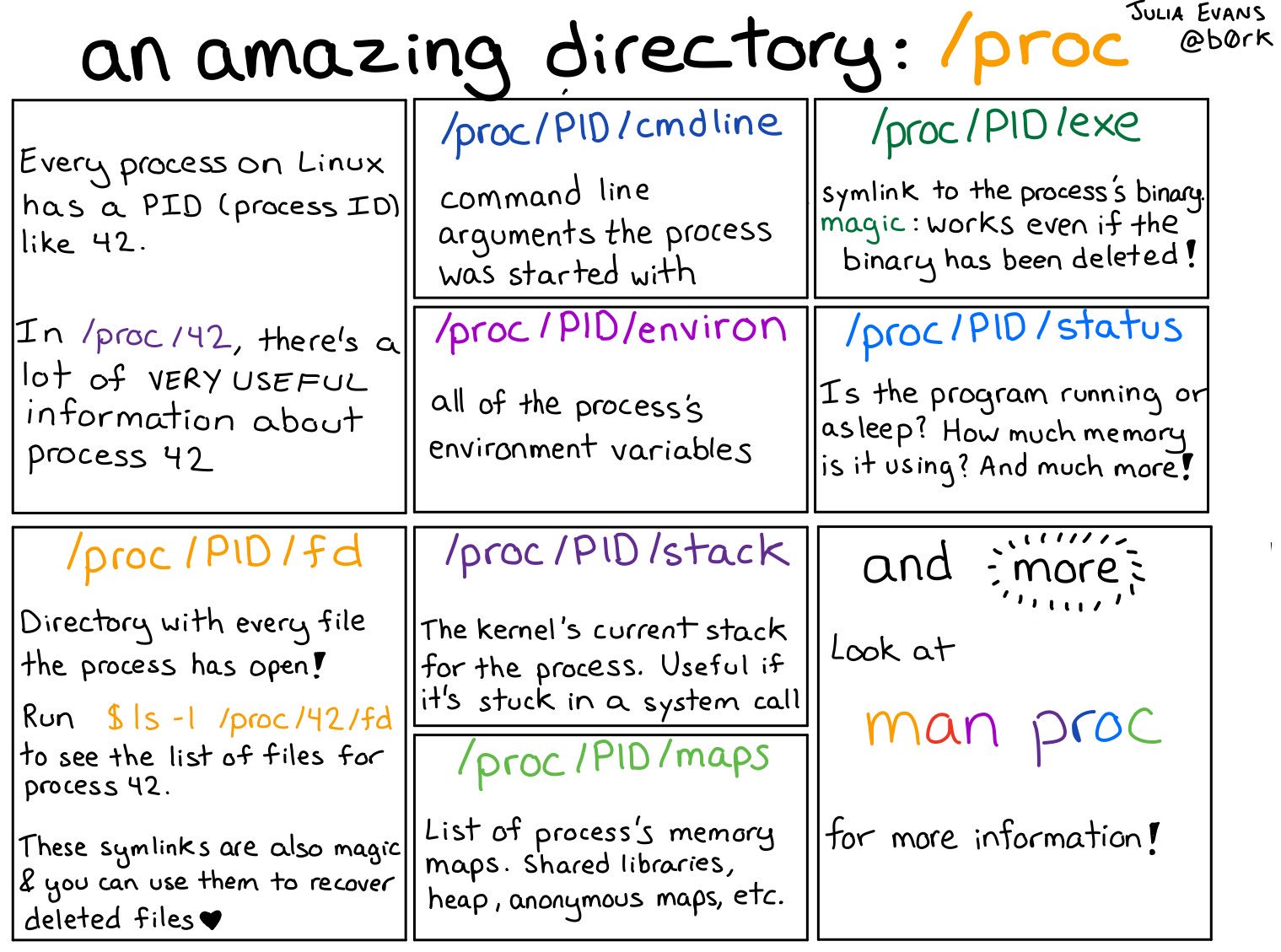
/proc
Figure © 2018 Julia Evans, all rights reserved; from julia's drawings. Displayed here with personal permission.
2.1. Processes
First approximation: Process ≈ program in execution
- However
- Single program can create multiple processes
- E.g., web browser with process per tab model
- What looks like a separate program may not live inside its own process
- Single program can create multiple processes
- However
- Reality: Process = Whatever your OS defines as such
- Unit of management and protection
- One or more threads of execution
- Address space in virtual memory, shared by threads within process
- Management information in process control blocks
- Access rights
- Resource allocation
- Miscellaneous context
- Unit of management and protection
2.2. Process Creation
- OS starts
- Check your OS’s tool of choice to inspect processes after boot
- User starts program
- E.g., touch, click, type, speak, shake
- Processes start other processes
- POSIX standard with Process management API; see (Hailperin 2019)
2.2.1. Bash as Command Line
Recall: Command line as interface to OS to execute processes
- Unix command line historically called “shell”
- Command line itself is a process
- Lots of shell variants; Bash from The Command Line Murders used here
Command line can (1) execute builtin commands and (2) create processes for other commands
- Builtin commands are executed internally
- Type
helpto execute one and see all of them
- Type
- Programs are executed as new child processes (requires system calls)
- E.g.,
cat,grep,less,man,ps - By default, while child process for program runs, process of bash waits (not on CPU but blocked) for return value of child
- E.g.,
- Builtin commands are executed internally
- Unix command line historically called “shell”
2.3. Process Control Block
- Similarly to thread control blocks
the OS manages process control blocks for processes
- Numerical IDs (e.g., own and parent)
- Address space
- Resources (shared by threads)
- E.g., file descriptors discussed next
- Security information
- Related to access rights
- And more, beyond course, e.g.:
- Interprocess communication with signals
2.3.1. Seeing Processes and Threads on Linux
Linux kernel offers
/proc(drawing) (man page offers details)Pseudo-filesystem as interface to Linux kernel data structures
Subdirectories per process ID (e.g.,
/proc/42) with details of process control block for process with ID 42
Process listing command
psinspects/proc- (Use
man psfor implementation-specific details, following options are for GNU/Linux) ps -eshows some details on all processes (IDs, time, etc.)- Option
-Ladds thread information, option-ffor “full format”, e.g.:ps -eLf - (“L” for “light weight process”, a synonym for thread;
column
LWPshows thread IDs)
- Option
ps -C <name>shows some details on all processes with the given name
- (Use
- Other OSs come with their own tools
3. File Descriptors
- Recall The Command Line Murders
cd clmystery/mysteryhead crimescene | grep Alicecrimescene\(\leadsto\)head\(\leadsto\)grep\(\leadsto\)console output
head crimescene > first10lines
grep Alice < first10linescrimescene\(\leadsto\)head\(\leadsto\)first10lines\(\leadsto\)grep\(\leadsto\)console output
- (Files are covered in Section 8.3 of (Hailperin 2019))
3.1. File Descriptors
OS represents open files via integer numbers called file descriptors
- Files are abstracted as named streams of bytes
File abstraction includes “real” files, directories, devices, network access, and more
- Typical operations:
open,close,read,write
- Typical operations:
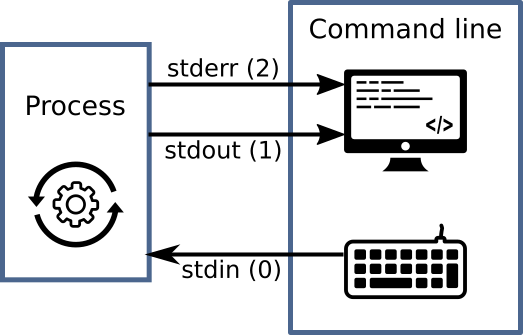
POSIX standard describes three descriptors (numbered 0, 1, 2) for every process
![Standard file descriptors]()
“Standard file descriptors” by Jens Lechtenbörger under CC BY-SA 4.0; using UXWing icons: keyboard, monitor, operations; from GitLab
- Standard input,
stdin(e.g., keyboard input) - Standard output,
stdout(e.g., print to screen/terminal) - Standard error,
stderr(e.g., print error message to terminal)
- Standard input,
3.2. Drawing on File Descriptors

File descriptors
Figure © 2018 Julia Evans, all rights reserved; from julia's drawings. Displayed here with personal permission.
3.3. Files/Streams for IPC
- IPC = Inter-process communication
- Communication between processes
- Files and streams enable communication
- (Next to other mechanisms, e.g., shared memory, signals, networking)
- Files provide persistent storage
- Written/created by one process
- Potentially accessed by other processes, communication, e.g.:
- Files with source code
- Write source code in editors (over time, different processes)
- Perform quality checks on source files with specialized tools (other processes, maybe passing results to editor)
- Compile source code to executable code
- Collect log messages from several processes in one file; analysis of file contents with alerting by separate process
- Files with source code
3.4. Redirection of Streams
Streams of bytes can be redirected
- E.g., send output to file instead of terminal
head names.txt > first10names.txt- (Recall: This command occurs in cheatsheet of The Command Line Murders)
- Code for
headinvokes system callsopenfilenames.txt, results in newly allocated file descriptorreadfrom file descriptor fornames.txtwritetostdout(opened automatically by default)
- Operator
>redirectsstdoutof process to filefirst10names.txt
- Also, lots of commands can access data on
stdinhead < names.txt- Operator
<redirects file tostdinof process; here, access ofnames.txtviastdin
- Operator
- E.g., send output to file instead of terminal
3.5. Streams for IPC
- Processes can communicate with pipelines/pipes
- One process connects stream as writer into pipeline
- Second process connects stream as reader from pipeline
- Pipelines (and files) are passive objects (used by processes)
- E.g., send
stdoutof one process tostdinof anotherhead names.txt | grep "Steve"- (Recall: This pipeline occurs in cheatsheet of The Command Line Murders)
- Here,
stdoutof process forheadconnected via pipe operator (|) withstdinof process forgrep- In contrast to files, pipes do not store data persistently
3.5.1. Drawing on Pipes
Pipes
Figure © 2016 Julia Evans, all rights reserved; from julia's drawings. Displayed here with personal permission.
3.6. File Descriptors under /proc
For process with ID
<pid>, subdirectory/proc/<pid>/fdindicates its file descriptors- (Recall:
<pid>is a number identifying a process) Entries are symbolic links pointing to real destination
Use
ls -lto see numbers and their destinations, e.g.:lrwx------ 1 jens jens 64 Jun 26 15:34 0 -> /dev/pts/3 lrwx------ 1 jens jens 64 Jun 26 15:34 1 -> /dev/pts/3 lrwx------ 1 jens jens 64 Jun 26 15:34 2 -> /dev/pts/3 lr-x------ 1 jens jens 64 Jun 26 15:34 3 -> /dev/tty lr-x------ 1 jens jens 64 Jun 26 15:34 4 -> /etc/passwd- Use of
/dev/pts/3(a so-called pseudo-terminal, which represents user interaction with the command line) forstdin,stdout, andstderr - Access of file
/etc/passwdvia file descriptor 4 - (If you are curious:
/dev/ttyis mostly the same as/dev/pts/3here)
- Use of
- (Recall:
3.6.1. A Quiz
4. Access Rights
4.1. Fundamentals of Access Rights
Who is allowed to do what?
System controls access to objects by subjects
- Object = whatever needs protection: e.g., region of memory,
file, service
- With different operations depending on type of object
Subject = active entity using objects: process
- Threads of process share same access rights
- Subject may also be object, e.g., terminate thread or process
- Subject acts on behalf of principal
- Principal = User or organizational unit
- Different principals and subjects have different access rights
on different objects
- Permissible operations
- Object = whatever needs protection: e.g., region of memory,
file, service
4.1.1. Typical Access Right Operations
In general, dependent on object type, e.g.:
- Files
- Create, remove
- Read, write, append
- Execute
- Change ownership
- Access rights
- Copy/grant
- Files
4.2. Representation of Access Rights
- Conceptual: Access (control) matrix
- Slices of access matrix
4.2.1. Access (Control) Matrix
- Matrix
- Principals and subjects as rows
- Objects as columns
- List of permitted operations in cell
4.2.2. Access Matrix: Transfer of Rights
Transfer of rights from principal JDoe to process P_1
Figure 7.12 (a) of (Hailperin 2019): copy rights
F_1 F_2 JDoe P_1 … JDoe read write P_1 read write ⋮
Figure 7.12 (b) of (Hailperin 2019): special right for transfer of rights
F_1 F_2 JDoe P_1 … JDoe read write P_1 use rights of ⋮
4.2.3. Capabilities
- Capability ≈ reference to object with access rights
- Conceptually, capabilities arise by slicing the access
matrix row-wise
- Principals have lists with capabilities (access rights) for objects
- Challenge: Tampering, theft, revocation
- Capabilities may contain cryptographic authentication codes
4.2.4. Access Control Lists
- Access Control List (ACL) = List of access rights for subjects/principals attached to object
- Conceptually, ACLs arise by slicing the access matrix column-wise
- E.g., file access rights in GNU/Linux and Windows (see Sec. 7.4.3 in (Hailperin 2019))
4.2.5. File ACLs
lslists files and directories- With option
-lin “long” form- Shortened ACLs
- Permissions not for individual users; instead, separately for owner, group, other
- Owner: Initially, the creator; ownership can be transferred
- Group: Users can be grouped, e.g., to share files for a joint project
- Other: Everybody else
- File type, followed by 3 triples with permissions
- File (
-), directory (d), symbolic link (l), … - Read (
r), write (w), execute (x) (for directories, “execute” means “traverse”) - Set user/group ID (
s), sticky bit (t)
- File (
ls -l /etc/shadow /usr/bin/passwd-rw-r-----1rootshadow2206 Jan 11 2024 /etc/shadow-rwsr-xr-x1rootroot68208 Feb 6 13:49 /usr/bin/passwd*
ls -ld /tmpdrwxrwxrwt14rootroot20480 Jun 8 13:20 /tmp
- Shortened ACLs
- With option
4.2.6. Drawing on File ACLs
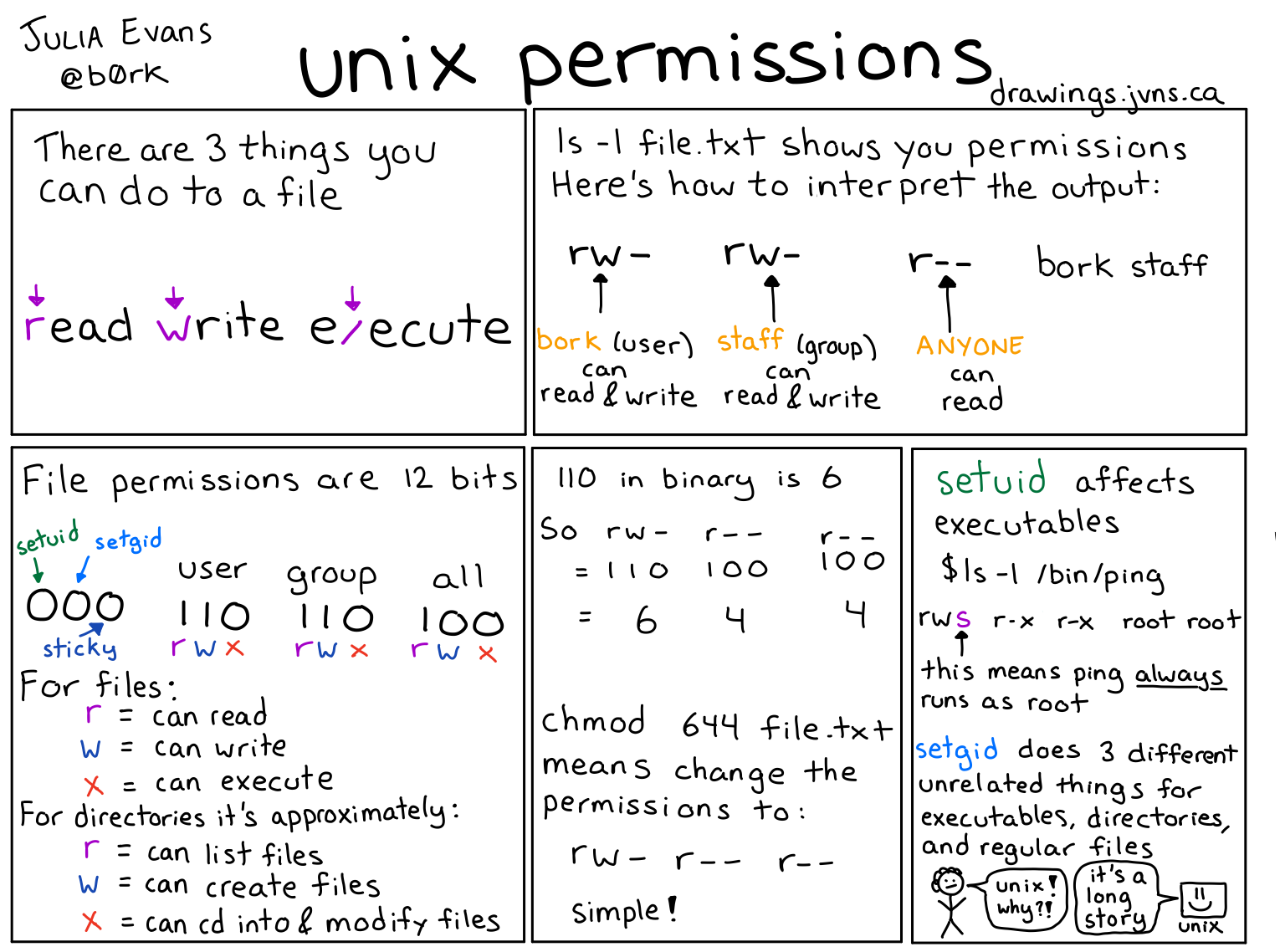
Unix permissions
Figure © 2018 Julia Evans, all rights reserved; from julia's drawings. Displayed here with personal permission.
4.2.7. File ACL Management
- Management of ACLs with
chmod- Read its manual page:
man chmod - (Default permissions for new files are configurable)
- (Beyond class topics, see
help umaskin bash)
- (Beyond class topics, see
- Read its manual page:
- Permissions with bit pattern or symbolically
- Previous drawing illustrates bit patterns
for
r,w,x - Symbolic specifications contain
- one of (among others)
u,g,ofor user, group, others, resp., - followed by
+or-to add or remove a permission, - followed by one of
r,w,x,s,t(and more)
- one of (among others)
- E.g.,
chmod g+w file.txtadds write permissions for group members onfile.txt
- Previous drawing illustrates bit patterns
for
5. Conclusions
5.1. Summary
- Process as unit of management and protection
- Threads with address space and resources
- Including file descriptors
- Isolation of virtual address spaces as protection mechanism
- Threads with address space and resources
- File access abstracted via numeric file descriptors as streams
- Redirection and pipelining for inter-process communication
- Access control restricts operations of principals via subjects on objects
- GNU/Linux file permissions as example for ACLs
- Access control as additional OS protection mechanism
5.2. Perspective
- Different access control paradigms exist
- Discretionary access control (DAC)
- Owner grants privileges
- E.g., file systems, seen above
- Mandatory access control (MAC)
- Role based access control (RBAC)
- Permissions for tasks bound to organizational roles
- E.g., different rights for students and teachers in Learnweb
- Permissions for tasks bound to organizational roles
- Discretionary access control (DAC)
5.3. Maybe in-class: Safety vs Security
- Selected pointers
- Safety: Protection against unintended/natural/random events
- Requires proper management, involves training, redundancy (e.g., hardware, backups), and insurances
- Security: Protection against deliberate attacks/threats
- Protection of security goals for objects and services against attackers
- Security goals and risk
- CIA triad with classical goals: Confidentiality, Integrity, Availability
- Many more, e.g., accountability, anonymity, authenticity, (non-) deniability
- E.g.: Processes on “your” system?
- Advanced persistent threats (APTs), rootkits
- Check externally, e.g., German Desinfec’t
- Design processes and management
- E.g., BSI in Germany and ISO standards: IT-Grundschutz
- Safety: Protection against unintended/natural/random events
Bibliography
License Information
Source files are available on GitLab (check out embedded submodules) under free licenses. Icons of custom controls are by @fontawesome, released under CC BY 4.0.
Except where otherwise noted, the work “Processes”, © 2017-2026 Jens Lechtenbörger, is published under the Creative Commons license CC BY-SA 4.0.