MX Challenges
(Usage hints for this presentation)
IT Systems, Summer Term 2026
Dr.-Ing. Matthes Elstermann
1. Introduction
- Part 1
- Part 2
- Part 3
2. Deadlocks
Did you play level “Deadlock” at https://deadlockempire.github.io/?
- There, you lead two threads into a deadlock…
2.1. Deadlock
Permanent blocking of thread set
“Gridlock” by Interiot~commonswiki and Jeanacoa under CC BY-SA 2.5 Generic; from Wikimedia Commons
- Reason
- Cyclic waiting for resources/locks/messages of other threads
- (Formal definition on later slide)
- Reason
- No generally accepted solution
- Deadlocks can be perceived as programming bugs
- Dealing with deadlocks causes overhead
- Acceptable to deal with (hopefully rare) bugs?
- Dealing with deadlocks causes overhead
- Solutions depend on
- Properties of resources (e.g., linearly ordered ones)
- Properties of threads (transactions?)
- Deadlocks can be perceived as programming bugs
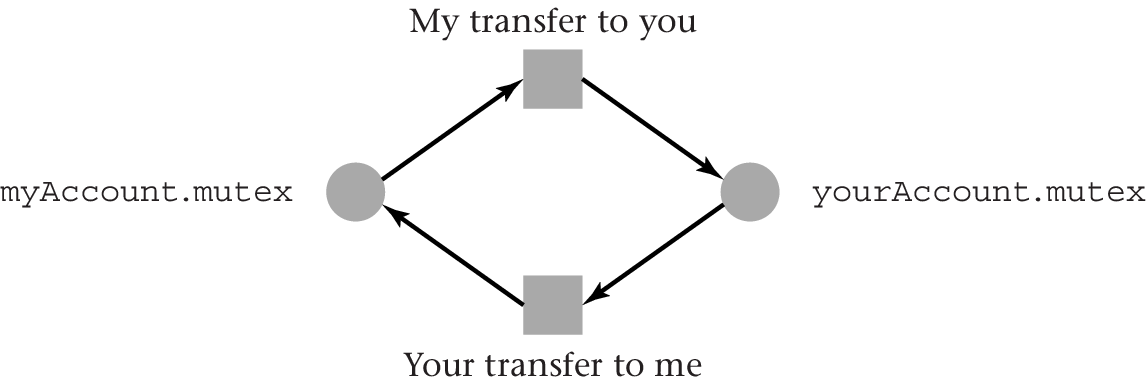
2.2. Deadlock Example
- Money transfers between bank accounts
- Transfer from
myAccounttoyourAccountby thread 1; transfer in other direction by thread 2
- Transfer from
- Race conditions on account balances
- Need mutex per account
- Lock both accounts involved in transfer. What order?
- “Natural” lock order: First, lock source account; then, lock
destination account
- Thread 1 locks
myAccount, while thread 2 locksyourAccount- Each thread gets blocked once it attempts to acquire the
second lock
- Neither can continue
- Deadlock
- Each thread gets blocked once it attempts to acquire the
second lock
- Thread 1 locks
2.3. Defining Conditions for Deadlocks
Deadlock if and only if (1) – (4) hold (Coffman, Elphick, and Shoshani 1971):
- Mutual exclusion
- Exclusive resource usage
- Hold and wait
- Threads hold some resources while waiting for others
- No preemption
- OS does not forcibly remove allocated resources
- Circular wait
- Circular chain of threads such that each thread holds resources that are requested by next thread in chain
2.4. Resource Allocation Graphs
- Representation and visualization of resource allocation as
directed graph
- (Necessary prior knowledge: directed graphs and cycles)
Nodes
![Figure 4.22 of (Hailperin 2019)]()
“Figure 4.22 of (Hailperin 2019)” by Max Hailperin under CC BY-SA 3.0; converted from GitHub
- Threads (squares)
- Resources (circles)
- (Choice of shapes is arbitrary, just for visualization purposes)
- Edges
- From thread T to resource R if T is waiting for R
- From resource R to thread T if R is allocated to T
- Fact: System in deadlock if and only if graph contains cycle
3. Deadlock Strategies
3.1. Ostrich “Algorithm”
- A joke about missing deadlock handling
- “Implemented” in most systems
- Pretend nothing special is happening
- (E.g., Java acts like ostrich)
- Reasoning
- Proper deadlock handling is complex
- Deadlocks are rare, result from buggy programs
- “Implemented” in most systems
(Refresh HTML presentation for other drawings)
3.2. Deadlock Prevention
- Prevent a defining condition for deadlocks from becoming true
Practical options
Prevent condition (2), “hold and wait”: Request all necessary resources at once
- Only possible in special cases, e.g., conservative/static 2PL in DBMS
- Threads either have no incoming or no outgoing edges in resource allocation graph → Cycles cannot occur
Prevent condition (4), “circular wait”: Number resources, request resources according to linear resource ordering
- Consider resources R_h and R_k with h < k
- Threads that need both resources must lock R_h first
- Threads that already requested R_k do not request R_h afterwards
- Requests for resources in ascending order → Cycles cannot occur
- Consider resources R_h and R_k with h < k
3.2.1. Linear Resource Ordering Example
- Money transfers between bank accounts revisited
- Locks acquired in order of account numbers
- A programming contract, not known by OS
- Suppose
myAccounthas number 42,yourAccountis 4711- Both threads try to lock
myAccountfirst (as 42 < 4711)- Only one succeeds, can also lock
yourAccount - The other thread gets blocked
- Only one succeeds, can also lock
- Both threads try to lock
- No deadlock
- (See Fig 4.21 in (Hailperin 2019) for an example of linear ordering in the context of the Linux scheduler)
3.3. Deadlock Avoidance
Dynamic decision whether allocation may lead to deadlock
- If a deadlock cannot be ruled out easily: Do not perform that allocation but block the requesting thread (or return error code or raise exception)
- Consequently, deadlocks do never occur; they are avoided
Classical technique
- Banker’s algorithm by Dijkstra
- Deny incremental allocation if “unsafe” state would arise
- Not used in practice
- Resources and threads’ requirements need to be declared ahead of time
- Banker’s algorithm by Dijkstra
3.4. Deadlock Detection
Idea
- Let deadlocks happen
- Detect deadlocks, e.g., via cycle-check on resource allocation graph
- Periodically or
- After “unreasonably long” waiting time for lock or
- Immediately when thread tries to acquire a locked mutex
- Resolve deadlocks: typically, terminate some thread(s)
Prerequisite to build graph
- Mutex records by which thread it is locked (if any)
- OS records for what mutex a thread is waiting
4. Further Challenges
4.1. Starvation
- A thread starves if its resource requests are repeatedly denied
- Examples in previous presentations
- Interrupt livelock
- Thread with low priority in presence of high priority threads
- Thread which cannot enter CS
- Famous illustration: Dining philosophers (next slide)
- No simple solutions
4.1.1. Dining Philosophers
- MX problem proposed by Dijkstra
- Philosophers sit in circle; eat and think repeatedly
- Two forks required for eating
- MX for forks
- Two forks required for eating
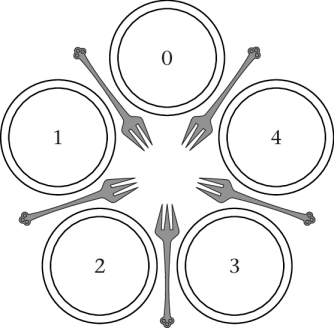
Dining Philosophers
“Figure 4.20 of (Hailperin 2019)” by Max Hailperin under CC BY-SA 3.0; converted from GitHub
4.1.2. Starving Philosophers
Starvation of P0
![Figure 4.20 of (Hailperin 2019)]()
“Figure 4.20 of (Hailperin 2019)” by Max Hailperin under CC BY-SA 3.0; converted from GitHub
- P1 and P3 or P2 and P4 eat in parallel
- Then they wake the other pair
- P1 wakes P2; P3 wakes P4
- P2 wakes P1; P4 wakes P3
- Iterate
- (Above sequence possible for algorithm in (Tanenbaum 2001); inspired by exercise in (Stallings 2001))
5. Conclusions
5.1. Priority Inversion Example
- Mars Pathfinder, 1997;
Wikipedia offers details
Robotic spacecraft named Pathfinder
![Sojourner Rover]()
“Sojourner Rover” by NASA under Public domain; from Wikimedia Commons
- With rover named Sojourner (shown to right)
- A “low-cost” mission at $280 million
- Bug (priority inversion) caused repeated resets
- “found in preflight testing but was deemed a glitch and therefore given a low priority as it only occurred in certain unanticipated heavy-load conditions”
- Priority inversion had been
known for a long time
- E.g.: (Lampson and Redell 1980)
5.2. Summary
- Concurrent access to resources leads to races
- Mutual exclusion for critical section prevents races
- Locks, monitors
- Keyword
synchronizedin Java- Cooperation via
wait()andnotify()
- Cooperation via
- Challenges such as deadlocks, starvation, priority inversion
Bibliography
License Information
Source files are available on GitLab (check out embedded submodules) under free licenses. Icons of custom controls are by @fontawesome, released under CC BY 4.0.
Except where otherwise noted, the work “MX Challenges”, © 2017-2026 Jens Lechtenbörger, is published under the Creative Commons license CC BY-SA 4.0.